For hackers.
-
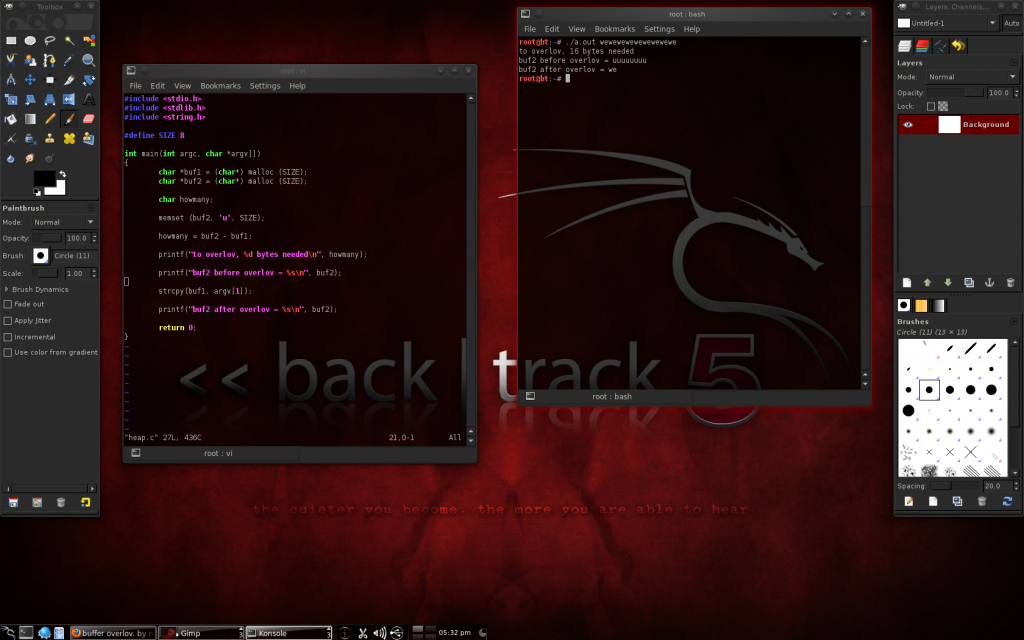
buffer overlov:
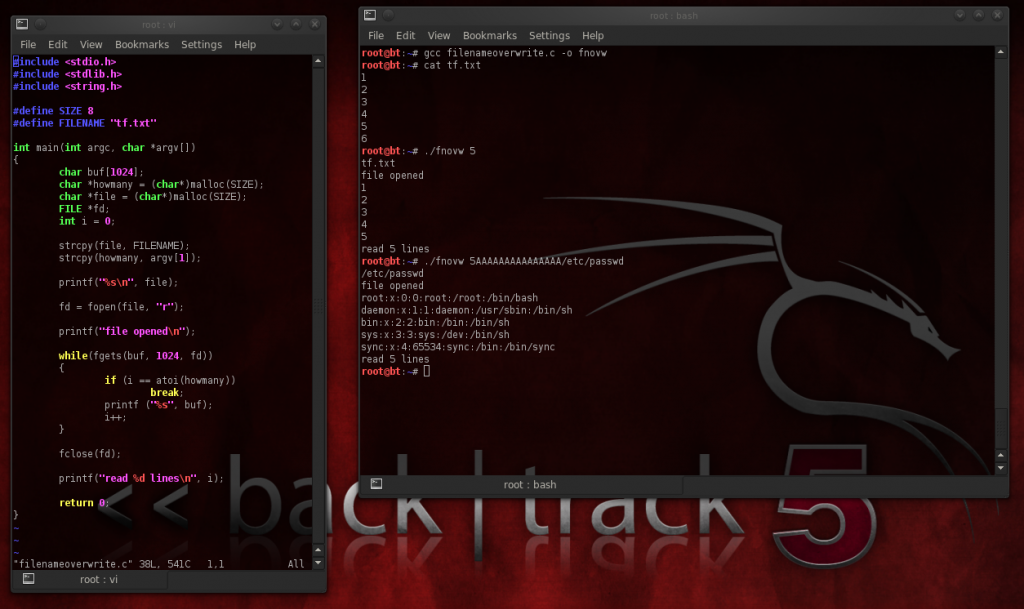
with file overwrite:
'file name overwrite to access private data'.
encrypted system passwords are in /etc/shadow.
unneccessary lines (such as debug printf) are danger to leave, for they give out information about hacker.
-
Buffer Overflow.
Shellcode passed via environment, application (bo) attacked to gain privileges.
Stack overflow to overwrite EIP (instruction pointer) stored on stack 'above' buffer 'buf', so when program returns from function, it restores registers and state. With new EIP value, it jumps to shellcode spawning command shell with privileges of attacked application.
0xbffffffa is stack's base address.
any application can be spawned this way (even 'custom made. fork and setuid open some possibilities'). Perhaps someone with privileges will run more than they have intended.
-
exercise on attacking applications.
knowing source code makes such hacks much easier.
simple words:
made program execute wrong part of code, logged in without knowing login and password.
technical details:
disassembled binary, checked address of conditional instruction ('if') part. In assembler it's 'je', or jump if equal.
then did stack overflow to overwrite login variable buffer and 4 registers including EIP (instruction pointer), redirecting program to inside conditional code, despite that condition was not met.